Here's a classic scenario:
Basically here you have your workstation, and in order to get to the internet, you need to go through an ISA server working as a proxy server filtering your content. Here's where your facebook, youtube, IRC, and so on, gets filtered.
We are going to create a tunnel between your workstation and your home computer, and redirect all your internet traffic from your workstation to your home connection, so you don't have any content filtering involved. For this, here's the list of components that are part of this solution:
- Workstation running Windows (XP/7)
- PuTTY
- Cntlm
- Home computer running OpenSSH (Windows/Linux)
- Router at home with port forwarding capabilities.
- Patience
So let's get started at home.
As I said, you need a host running OpenSSH. If you're using Linux, you have the simplest path to install it, and probably, you already have it. If you're using Windows, you have two options that may suit you:
- Try to install OpenSSH in Windows
- Install a Virtual Machine running linux
I consider the second option to be the easiest one. Not only because SSH is way simpler to configure, manage and install in Linux, but also because it's always nice to have a Linux at home to mess around.
If you're thinking about the first one, you can use this guide that, even though is aimed for Windows server 2003, it works for Windows XP: Installing OpenSSH for Windows 2003 Server - How to get it working.
At the end of the day, what we need is a box listening in port 22 and ready for connections.
Once we have our SSH host, we are going to need our home router to forward our connections from outside to our SSH host. Since ISA server only lets encrypted traffic go through port 443 (SSL), we need to forward port 443 for incoming traffic from internet to port 22 in our SSH host.
There's too many ways to do this according to which router you have. Basically, every port forward is going to ask you the following info:
Destination IP: Your SSH Host ip.
Source Port: 443
Destination Port: 22
If you want the exact steps for your router, you can use this awesome page: http://portforward.com/. Here you'll find guides for a LOT of routers.
So now you have your home computer waiting for connections. What you will need now is to find out your Public IP so you'll know where to connect to from your workstation. Just Google "What's my ip" and you'll find a zillion results.
Now let's take care of our workstation.
In our workstation we're going to use two pieces of software: PuTTY and Cntlm. PuTTY is the software that actually builds the tunnel, but there's a problem: ISA server uses NTLM for authentication which PuTTY doesn't support. That's where Cntlm comes as a solution. Cntlm is proxy we install in our own work computers to solve the authentication problem.
First of all, let's download it from here:
http://cntlm.sourceforge.net/
Once you install it, you'll see that there's not much to be done but to edit the cntlm.ini. Here, you will need to change a few lines:
Username Your Username at work (e.g. name.lastname)
Domain Domain your workstation is using (e.g. contoso.com)
Password Password for that same user (e.g. P@ssw0rd)
Proxy Work ISA proxy server (e.g. proxy.contoso.com:8080)
Listen 5555
Domain Domain your workstation is using (e.g. contoso.com)
Password Password for that same user (e.g. P@ssw0rd)
Proxy Work ISA proxy server (e.g. proxy.contoso.com:8080)
Listen 5555
Leave the rest for the ini file unedited. Save it, and close it. Now, just run the cntlm.exe. Don't worry, you won't see anything because it runs in the background. You can see it in the Process list in the Task Manager. Now you have CNTLM listening in port 5555 and it will deal with your proxy authentication.
Now let's deal with our final part of this guide, building the tunnel with PuTTY. First of all, install PuTTY if you don't have it (duh) and open it.
You start in the Session category. Write down your Public IP in "Host Name" text box and 443 in "Port".
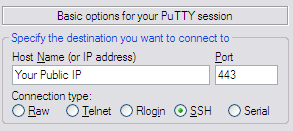
Now go to Connection > Proxy. Here you only need to select Proxy Type: HTTP, and then write down the following:
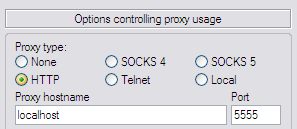
Leave the rest as it is. Now move on to SSH > Tunnels. Here you have to write 1080 in "Source Port", select Dynamic and click Add. You will have something like this:
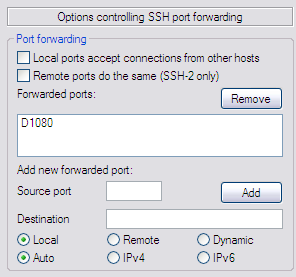
Now, let's go back to Session category at the top of the list. In Saved sessions, write something descriptive for this tunnel like "Home" or "SSH tunnel", whatever you want. Then click Save. This way, next you only have to double click the session and it will connect automatically to it.
And that's it! You will have a new window showing the following:

That means that you're able to connect to your home SSH host and your tunnel is ready for use. Now you will need to configure your browser proxy settings.
Here's how it should look:
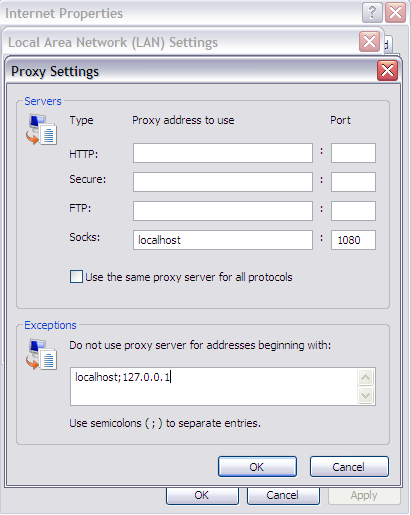
Now try to open a once-filtered webpage and if you open it, you'll be using your home connection! I hope you liked this guide and let me know if you have any doubts!

ty for advice, followed your blog for more information :)
ReplyDeleteExcellent, works like a charm, thanks !
ReplyDelete